June 27, 2024
NTT Data Group, Inc.
NTT Data Group has established a virtual server implementation method that can encrypt data under computation, including sensitive information, such as memory data, which has not been sufficiently encrypted in terms of data handling and computation of confidential information is a challenge to be solved. This will ensure data sovereignty from an economic security perspective on a sovereign cloud. The company aims to launch this function for virtual servers using this implementation method to private companies, government agencies, and local governments in Japan and overseas, in the NTT Data Group and its group companies' cloud services, by fiscal 2025.
In recent years, there has been growing demand for a sovereign cloud that enables nations and companies to protect and control their sovereign rights from the perspective of economic security. Guaranteeing "data sovereignty," which is required to ensure adequate control over access to data on cloud services, is a crucial prerequisite for achieving the goal of sovereign cloud services. For instance, large-scale cloud services with a global presence often have their headquarters or data centers located outside the country's laws and regulations, resulting in the risk of data leakage owing to the disclosure of user data. To handle highly confidential information, such as personal information, intellectual property, and tradable information, when operating a system on cloud services, ensuring data sovereignty is essential, and appropriate access controls must be implemented in the cloud service data.

Background
In the future, NTT Data Group and its domestic and overseas group companies will aim to launch the virtual server functionality based on this implementation method by fiscal 2025, targeting private companies, government agencies, and local governments in Japan and overseas through their cloud services.Note 1
The challenge of properly controlling access to data on cloud services is that data under computation is not sufficiently encrypted. While data on storage and on the network is encrypted in conventional cloud services, the computed data on memory is not sufficiently encrypted, which poses a significant risk of data leakage.
In response to this situation, NTT Data Group has been working on verifying related security technologies since fiscal 2023 and has now established a virtual server implementation method that can encrypt data under computation.
Overview of the implementation method:
The implementation method established this time uses confidential computing, a security technology that encrypts computed data in memory to encrypt computed data on the virtual server's memory. In addition to encrypting computed data, the virtual server provided has more complete encryption of data on its storage and features a configuration validation and tamper detection function, preventing data access by infrastructure operators.
1. Encryption of data under computation
Trusted Execution Environment (TEE), the core technology of confidential computing, encrypts computed data on virtual servers, preventing software executed by physical servers, such as hypervisors, etc., from reading or altering the data. Note 2which utilizes generated AI, members who newly develop a manufacturing process for laundry detergent for clothing can easily search and utilize skilled workers' technology, knowledge, and know-how and, thus, support the efficient execution of the business task.
2. More complete encryption of data on the boot disk
Data stored on the virtual server's boot disk is encrypted. In the previous disk encryption/decryption processing, the data was temporarily unencrypted, but in this implementation method, data encryption/decryption processing is executed inside the virtual server that is secured by TEE, and data is always encrypted outside the virtual server. Note 4
3. Configuration validation and tamper detection of the virtual server
When the virtual server starts up, a key information is required to decrypt confidential data. In this implementation method, when providing key information to the virtual server, the virtual server's running environment and basic software are verified by the Attestation Service, an external service with a high level of reliability. This prevents confidential data leaks caused by data encryption setting oversights or software tampering by third parties, etc. Note 5
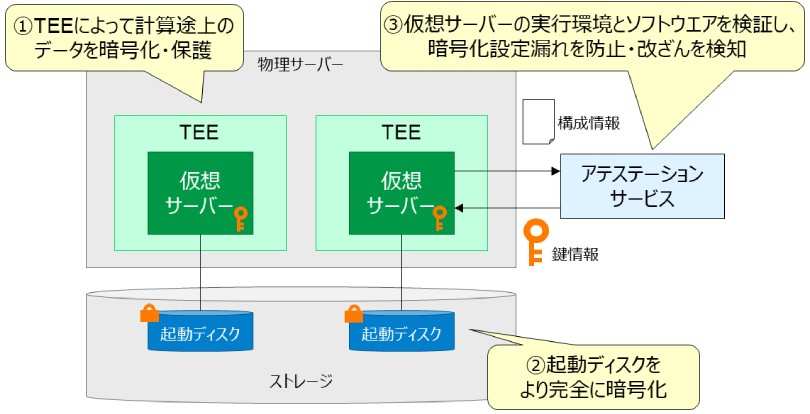
Figure: Overview of the implementation method's functions
Use cases are envisaged for the established implementation method.
- Cases where handling of highly confidential information such as personal information, intellectual property, and highly fungible information is being considered.
- Cases where handling of highly confidential information on the cloud is being considered.
- Cases where security measures against data leakage and malicious tampering by third parties and others are to be strengthened.
- Cases where stronger access restrictions on system data from cloud service providers or IT system providers are desired.
- Cases where encryption and protection of IT system data can be achieved without relying on specific service providers or IT system providers.
Future Prospects
The NTT DATA Group aims to start the provision of virtual servers that allow encryption of data in computation by introducing the established implementation method into “OpenCanvas,'' a cloud service offered by NTT DATA by 2025.In addition, we plan to provide technical support for introducing similar functions into customer systems that require more robust data protection for confidential information in on-premises IT systems.
Notes
- Note 1: A “Sovereign Cloud” is a cloud service that is controlled and maintained by a country or company, generally with three aspects of sovereignty:
- Data sovereignty: the ability to control access to data stored in the cloud and limit the geographic location of data;
- System sovereignty: the ability to maintain ongoing availability of software and hardware making up the system;
- Operation sovereignty: the ability to maintain transparency in operation and remain unaffected by regulations of other countries.
- Note 2: A “Trusted Execution Environment” is a technology that allows access to specific data only by trusted applications.
- Note 3: A “Hypervisor” is software used to create, operate, and manage virtual servers.
- Note 4: A “boot disk” is a disk that stores basic software and data for virtual servers such as operating systems.
- Note 5: An “attestation service” is a service that verifies the consistency of the operating environment and software running within virtual servers.
For inquiries regarding this matter,
Contact information for products and services.
NTT Data Group, Inc.
Technical Development Division
IOWN Promotion Room
Tanaka, Kajinami
TEL:050-5546-9741

